Grep and Regular Expressions (Regex)
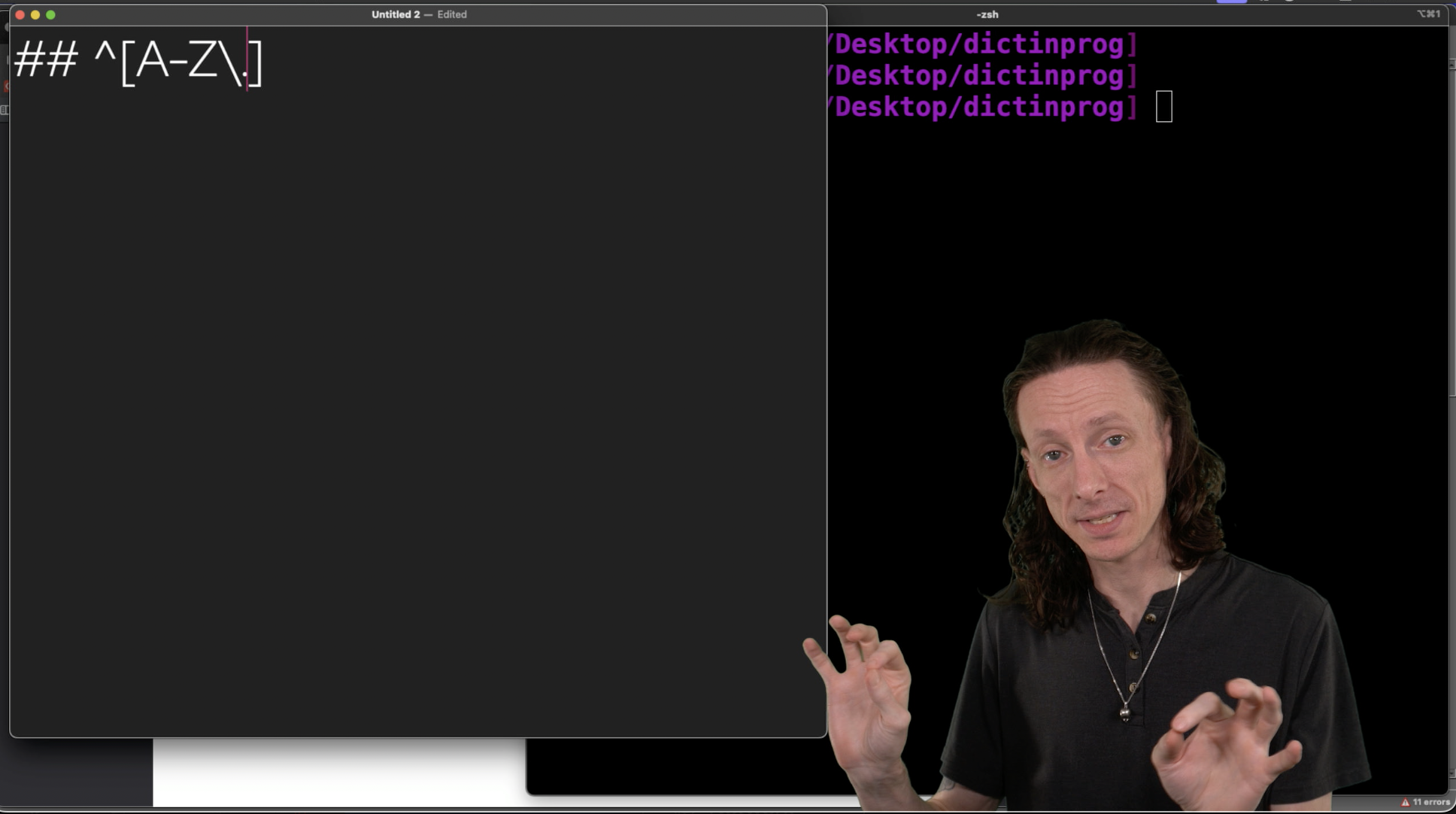
We use regex to extract acronyms. This will ultimately form a vocabulary for AI transcription models to enhance their accuracy with IT and technical topics.


We use regex to extract acronyms. This will ultimately form a vocabulary for AI transcription models to enhance their accuracy with IT and technical topics.

Installing ad, tracker, and threat intelligence domain blocklists

Install Pi-Hole with initial configuration. Add white-listed domains prior to incorporating blocklists in Part 4

Managing updates and host firewall

Initial OS installation and network setup for Raspberry Pi

Brief overview of vulnerability management and scanning